As cyber threats grow more sophisticated and digital infrastructures become more complex, the traditional perimeter-based approach to security is no longer sufficient. This evolution has brought about a paradigm shift toward a Zero Trust (ZT) security model, which fundamentally rethinks how organizations protect their networks and data. Unlike conventional models, Zero Trust operates on the principle that no user, device, or application should be automatically trusted—regardless of whether it is inside or outside the network perimeter. Instead, it emphasizes continuous verification, strict access controls, and robust encryption, which have become essential in defending against modern cyber threats.
For commercial industries and federal agencies alike, adopting a Zero Trust framework is now a priority to ensure comprehensive data protection. The National Institute of Standards and Technology (NIST) has been instrumental in shaping the development of Zero Trust, offering detailed guidelines and frameworks that help organizations build secure, resilient digital architectures. These NIST guidelines stress key principles such as least privilege access, encryption, and continuous monitoring, laying the foundation for robust, scalable security solutions.

The Zero Trust framework is structured around several essential pillars that provide a comprehensive security approach, as outlined by NIST and expanded in the CISA Zero Trust Maturity Model. These pillars ensure that security is enforced across all facets of a network, from user authentication to data protection, creating a robust and resilient cybersecurity posture:
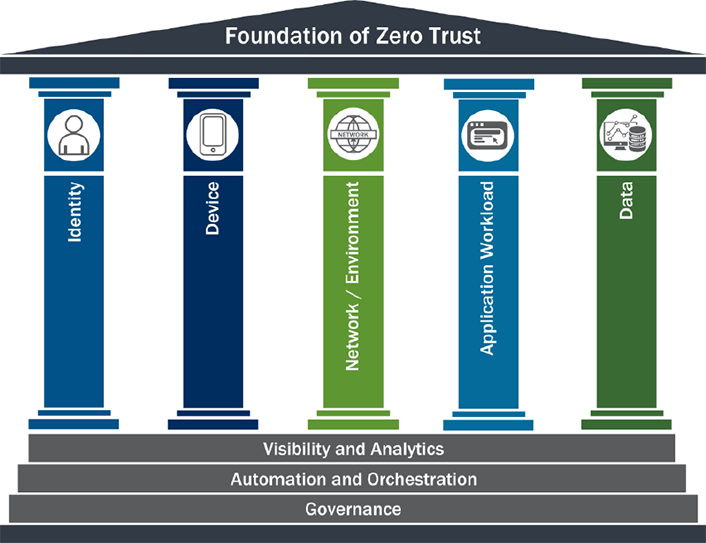
NIST’s Special Publication 800-207 outlines the Zero Trust Architecture (ZTA) and provides a structured approach for organizations to adopt this model. It emphasizes the importance of identity management, encryption, and continuous monitoring to build resilient systems. This guidance has been instrumental for federal agencies in adopting Zero Trust, with specific mandates from the U.S. government to implement these strategies. For instance, the Biden administration’s 2021 Executive Order on Improving the Nation’s Cybersecurity requires federal agencies to transition to a Zero Trust Architecture, compelling entities to follow NIST guidelines closely.
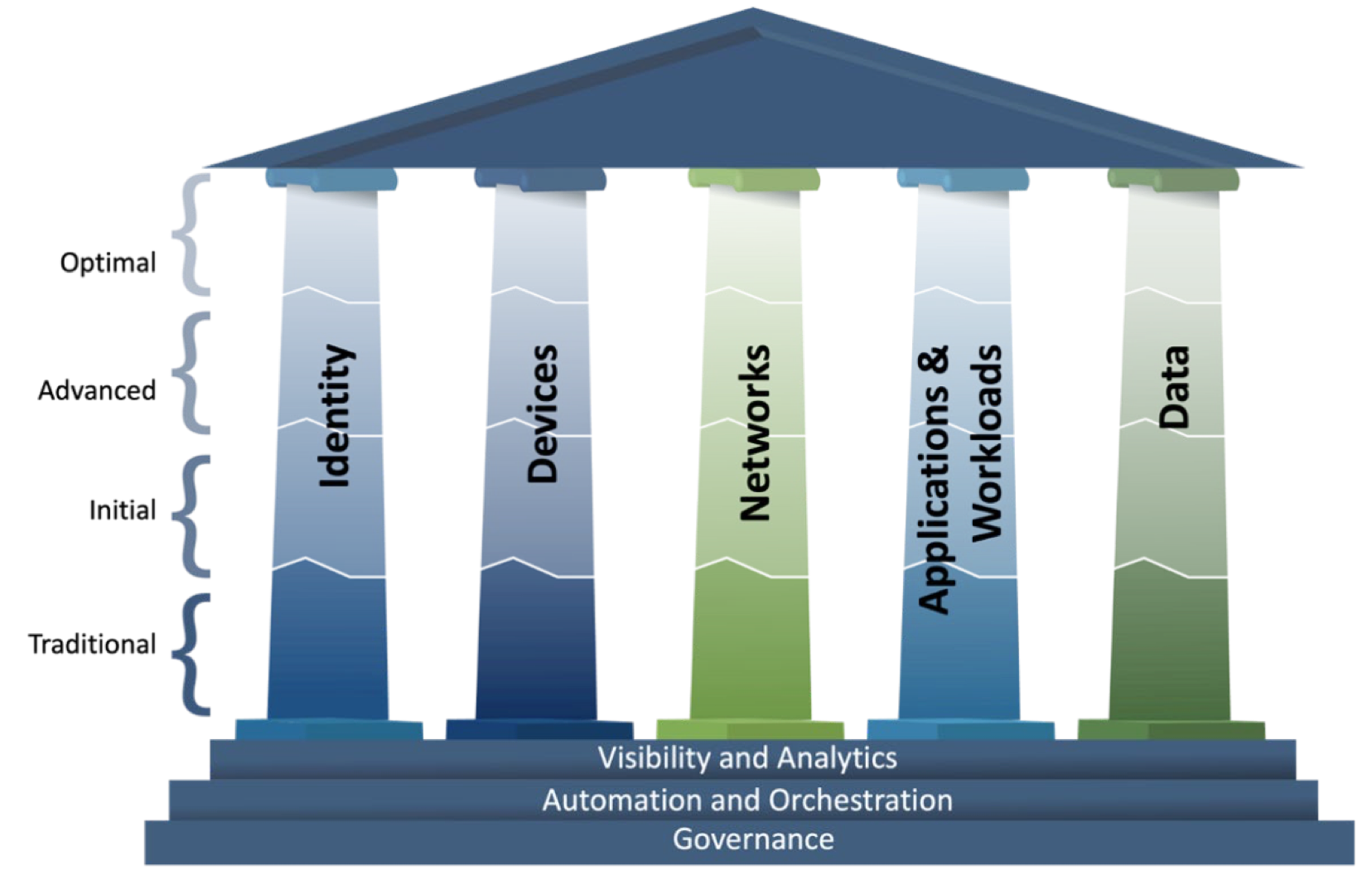
The adoption of Zero Trust frameworks has been instrumental in enhancing cybersecurity across various sectors. Several organizations, from tech giants to federal agencies, have implemented Zero Trust models to address the growing complexity and scale of digital threats. These real-world examples illustrate how effective Zero Trust principles can be in securing data, networks, and operations, and they serve as valuable blueprints for other entities looking to bolster their cybersecurity posture.


Google implemented a Zero Trust framework called BeyondCorp to eliminate the need for traditional VPNs, allowing secure remote access without relying on perimeter defenses. BeyondCorp emphasizes identity-based access control, continuously verifying user and device identity before granting access to applications, regardless of the network location.
The success of BeyondCorp has inspired other organizations to adopt similar approaches, proving that shifting from a network-centric to an identity-centric model can provide robust security without compromising user experience. This model supports scalable remote work, making it a valuable blueprint for companies facing similar challenges in today’s remote and hybrid work environments Cloud Security Transformation.
Accenture moved to a cloud-based Zero Trust model, implementing strict identity verification and multi-layer security protocols. Their approach includes continuous monitoring and micro-segmentation, allowing the company to manage access across both on-premises and cloud-based systems securely.
This model has enabled Accenture to ensure secure collaboration between different environments, reducing vulnerabilities and attack surfaces. The transformation showcases how Zero Trust can enhance security in complex, distributed cloud environments while supporting scalability and business agility. Accenture’s implementation highlights the importance of integrating Zero Trust with cloud infrastructure to safeguard sensitive data and operations across multiple platforms.
Following federal mandates, agencies like the Department of Defense (DoD) , Department of Homeland Security (DHS), and Department of Energy (DOE) have actively integrated Zero Trust principles to secure their networks. This includes rigorous authentication and micro-segmentation to protect sensitive data against insider and external threats.
Federal initiatives have further solidified the importance of Zero Trust in cybersecurity strategies. The Biden Administration’s Executive Order on Improving the Nation’s Cybersecurity mandates that federal agencies adopt Zero Trust Architecture. The Office of Management and Budget (OMB) released a Zero Trust strategy that requires agencies to achieve specific Zero Trust goals by the end of Fiscal Year 2024. Key requirements include implementing phishing-resistant multi-factor authentication (MFA), device-level security checks, and consolidating identity authentication systems to ensure secure, streamlined access across federal systems
The Cybersecurity and Infrastructure Security Agency (CISA) has also released its Zero Trust Maturity Model, which serves as a roadmap for federal agencies and private organizations to transition to a Zero Trust framework. This model emphasizes strong encryption, risk-based access control, and continuous monitoring, helping organizations scale their security measures based on unique operational requirements.
Vistory Secure has meticulously aligned its cybersecurity practices with NIST guidelines, integrating the pillars of Zero Trust into its flagship platform, MainChain. This strategic approach ensures a robust security framework that is both adaptive and resilient, particularly suited for digital manufacturing environments. The MainChain platform exemplifies how Zero Trust principles can be effectively applied to safeguard sensitive data and processes, helping organizations manage risks while enhancing operational efficiency. Here’s how MainChain incorporates key elements of Zero Trust:


MainChain emphasizes encryption and stringent access controls to secure data at every stage of production. By encrypting data both in transit and at rest, MainChain ensures robust intellectual property (IP) protection and maintains the integrity of sensitive information. The platform employs continuous authentication, verifying the identity of users and devices each time they interact with the system. This reflects the core Zero Trust principles of identity verification and least privilege access, where no user or device is trusted by default. This approach mitigates the risks of unauthorized access, data breaches, and insider threats, aligning closely with NIST’s focus on secure data handling and strict access controls.
Vistory Secure’s MainChain platform segments critical manufacturing operations into isolated network zones, minimizing the potential impact of breaches by containing threats within specific segments. Network segmentation reduces attack surfaces and prevents lateral movement across the network, a key tactic for limiting exposure to vulnerabilities. Additionally, MainChain’s encryption protocols ensure that data remains secure and traceable throughout its lifecycle, providing transparency and compliance across the entire supply chain. This level of segmentation and data security meets the stringent standards set by federal guidelines, including NIST and the CISA Zero Trust Maturity Model, ensuring that businesses can maintain robust defenses without compromising operational efficiency.
Vistory Secure integrates NIST’s guidelines directly into its platform, making compliance a built-in feature rather than an afterthought. Through continuous monitoring and real-time alerting, MainChain can quickly identify and respond to security incidents, ensuring resilience against emerging threats. This proactive stance is critical in sectors like defense and aerospace, where the stakes are high, and security breaches can have severe consequences. By adhering to compliance standards such as those outlined by NIST and supporting CISA’s Zero Trust Maturity Model, Vistory Secure facilitates scalable security frameworks that can adapt to diverse operational environments. This makes MainChain an ideal choice for organizations needing to meet strict regulatory requirements, whether in the commercial or federal sector, including the Department of Defense (DoD).
Vistory Secure’s MainChain platform is more than just a tool for securing digital manufacturing; it embodies the principles of Zero Trust to offer a holistic security solution. By integrating identity verification, encryption, segmentation, and compliance into a seamless platform, Vistory Secure enables organizations to stay ahead of evolving cybersecurity challenges. The alignment with NIST’s established frameworks ensures that companies using MainChain can build a resilient, Zero Trust architecture that secures sensitive data, protects intellectual property, and facilitates trust across digital supply chains.
The adoption of Zero Trust principles is no longer optional, especially for organizations handling sensitive data across various sectors. Guided by NIST’s comprehensive guidelines and reinforced by federal mandates, Zero Trust has become a cornerstone of modern cybersecurity. Vistory Secure embraces these principles, integrating advanced encryption, stringent authentication, and continuous monitoring into its MainChain platform.
By focusing on the core pillars of Zero Trust and aligning with federal strategies like the CISA Zero Trust Maturity Model, Vistory Secure offers robust, scalable solutions that enhance security without compromising operational efficiency. As cyber threats continue to evolve, the Zero Trust approach ensures that organizations are equipped to protect their assets, maintain compliance, and stay resilient against potential breaches.
Vistory Secure’s commitment to Zero Trust provides peace of mind for the commercial industry and U.S. federal agencies, including the Department of Defense, proving that secure, seamless, and reliable digital manufacturing is achievable.
Learn More
Our comprehensive suite of products ensures that your manufacturing processes are secure, compliant, and efficient, meeting the demands of modern industrial challenges. Let Vistory Secure be your trusted partner in achieving excellence in manufacturing.
Are you interested in Vistory or would you like more information?
Contact us or fill in this form.